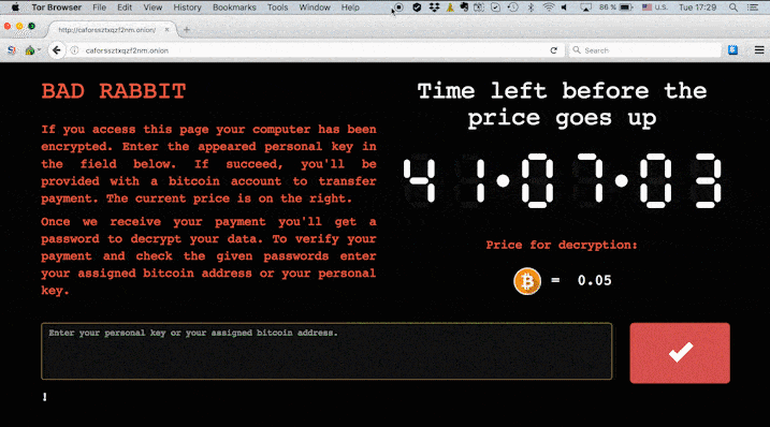
The latest malware is being called Bad Rabbit and, according to Kaspersky, is targeting both consumers and businesses. So far it has observed attacks in Russia and Ukraine. It posted the screenshot below on its blog. ESET has reported that the Kiev metro and Odessa airport has been hit by a new version of the infamous Diskcoder ransomware – which could also be Bad Rabbit at work.
The malware appears to be automatically downloaded when users visit legitimate websites, but as it doesn’t use any exploits as with previous ransomware, it relies on the user to run the program manually. It poses as an Adobe Flash installer. When the program is run, it displays a similar message to other ransomware and tells users to send just under $300 to a Bitcoin account. ESET says that Turkey, Bulgaria and other countries in addition to Russia and Ukraine are affected. There’s also the ongoing threat from the group responsible for leaking the vulnerabilities for WannaCry. Shadow Brokers, as it’s called, had already said it would leak more vulnerabilities and a Reuters report outlined the blog post from the group which says it is “setting up a monthly data dump” that it will sell to anyone willing to pay. It says that the exploits will enable criminals to code malware that will break into web browsers, phones, routers and Windows 10 systems. However, you can use our tips below to help keep your computers and files safe.
What is ransomware?
It’s a malicious program that’s like a computer virus. It’s designed to scan your hard drives and encrypt as many files as it can so you can’t access them. The files are still there and you have to pay a sum – the ransom – in order to get your files back. This is usually done via Bitcoin, as it’s anonymous. Related article: Best antivirus Sometimes, manual human intervention is required of the hackers to decrypt your files once you’ve paid. But since you’re dealing with criminals, there’s no reason to think they will do what they promise. So most experts recommend you don’t pay.
How does ransomware work?
Like a lot of malware, it can arrive as an email attachment. This method – relies on computer users opening the attachment, or clicking on a link in an email, which causes the program to run. People often open these attachments or click links out of curiosity, because the sender is someone in their address book. So the best advice is not to open anything you don’t completely trust. In the case of Petya, the attack targets system administrators of corporate networks, as it needs to get access to those high-level credentials in order to take control of as many other computers on the network as possible. This means than even if all machines have been patched with the Microsoft update from March 2017, there’s still a chance it can succeed. Some ransomware overwrites the MBR section of the computer’s hard disk – the Master Boot Record – which prevents Windows from booting, as well as stopping access to the files. On occasion, fixes or tools have been released for victims to get their data back. In the case of Bad Rabbit, as explained above, it’s said to arrive as a “drive-by download” which means it’s automatically saved to your hard disk when you visit a website. However, it appears to be harmless in this state and can be deleted. It’s only if you run the program (which masquerades as an Adobe Flash installation program) that it can get to work encrypting your files.
Which versions of Windows are affected?
Unlike previous ransomware, the indications are that Bad Rabbit doesn’t use any of Windows’ vulnerabilities. So although this means that every version of Windows is “affected” it’s actually the user that can cause the damage by manually running the downloaded program. So be extremely cautious of what you click on, and be sure your antivirus is up to date. The recent NotPetya attack mainly targeted businesses using the the same ‘EternalBlue’ vulnerability as WannaCry. Microsoft issued a patch to fix that security hole for all versions of Windows in March 2017. Since Windows defaults to installing updates automatically, that meant most home computers were safe. Businesses which turn off the feature could still be at risk if they haven’t installed the patch. If your computer runs Windows 10, it should be protected, too. Microsoft even issued a security patch for Windows XP and Windows 8 – a very unusual step for unsupported operating systems – which you can download from the links on Microsoft’s blog. You can check if your computer has the necessary patch installed using this free tool which you can download from our German sister site PCWelt (the tool is in English).
How can I protect my files from ransomware?
If you have Windows Update enabled then your PC should be protected from existing versions of ransomware. However, this doesn’t mean it’s 100 percent secure – you should still follow our advice below. If you’re not sure if your computers are up to date, then open the Control Panel (you’ll find a link in the Start menu) and search for Windows Update. Click through to Windows Update and you’ll be able to check if it’s enabled or not. There should be a button ‘Check for updates’ which you can click to force Windows to search and install critical updates. But don’t stop there, sit back and consider you’re safe. Follow our advice to keep your files safe from ransomware.
Back up!
The best protection is to have at least one (if not two) copies of any files you can’t afford to lose. Photos, home videos, financial documents and other files that can’t be replaced should be backed up regularly. Ransomware is often clever enough to scan your home network and infect other computers and even network storage drives (NAS drives) so it’s really important to make a backup on a USB stick or external hard drive that you disconnect and keep safely somewhere. You can find our pick of the best backup software here.
Don’t open attachments
You, as the computer user, are often the weak link in the chain. Windows and antivirus software – see below – can help to protect you from ransomware attacks, but you can help yourself by being vigilant about which email attachments you open, which links you click and which downloaded files you run. Typically, emails from hackers won’t contain a personal message, or it will be so generic that you can’t be sure it’s really from the person in the ‘sender’ field. In WannaCry’s case, at least some of the emails pretended to be an important email from a bank about a money transfer. Either just delete the email, or call the sender and ask them if they sent the email and what is in the attachment, or on the other end of the link. Unless you are absolutely sure the attachment is safe, don’t click on it.
Won’t antivirus software protect me from ransomware?
Most but not all antivirus software now contains ‘anti-ransomware’ that should help protect your PCs and laptops from WannaCry and other ransomware. That’s why it’s important not to rely just on Windows’ own security but to add an extra layer of protection. Check out our list of the best antivirus to make sure you’re running one of our recommended packages. Our favourite is BitDefender, but there are plenty of other great options to choose from too.
My PC is infected with ransomware. What should I do?
First, don’t pay the ransom. It only encourages the criminals – getting paid is their end game. And there’s no guarantee you will get your files back even if you do pay. If you have a backup of your files, you may be able to restore your machine to factory settings using a hidden recovery partition. Or it might be a case of reinstalling Windows. Then you’ll have to reinstall your apps and copy over your backed-up files. “One of the best protection mechanisms are patches”, said Marty P. Kamden, CMO of NordVPN. “Another way to protect yourself is to disrupt a system before it boots, as the ransomware runs on boot. After the device gets infected with a ransomware, it will wait for about an hour until reboot. Reboot is required for a malware to encrypt the system, so in certain cases, if the device gets terminated in the encryption process, it gets disrupted and information can be saved.” His advice is also to avoid clicking on any warning messages, instead closing them down using a keyboard command (such as Alt + F4) or right-clicking on the icon on the Taskbar and closing them that way. Another thing to protect your PC (and phone) from is the Meltdown and Spectre flaw. Read more abou Meltdown. Jim has been testing and reviewing products for over 20 years. His main beats include VPN services and antivirus. He also covers smart home tech, mesh Wi-Fi and electric bikes.